Product Security Onboarding
1. What is “Product Security” in SaaS?
- Protecting customer data from breaches, misuse, or accidental loss.
- Covering both technology (encryption, access control, monitoring) and processes (policies, vendor checks, incident handling).
- Demonstrated via recognized certifications & frameworks — these give customers proof we follow industry standards.
2. Key Certifications & Frameworks (What’s Out There)
(you get audited, get a formal certificate, can show customers)
- SOC 2 Type II – US SaaS trust standard, very common in procurement.
- ISO/IEC 27001 – International information security management certification.
- ISO/IEC 27701 – Privacy management (pairs with ISO 27001).
- FedRAMP Moderate – Required if selling to US federal agencies (government cloud).
- CMMC Level 2 – Required for Department of Defense-related contracts.
- PCI DSS SAQ – Payment card security compliance (usually handled by payment processor, but you still attest).
- CSA STAR Certification – Cloud security certification recognized globally.
Frameworks & Compliance Standards
(best practices, often referenced in RFPs; you align to them)
- NIST Cybersecurity Framework (CSF) – US government–favored baseline for managing cybersecurity risk.
- NIST SP 800-53 – More detailed control set for government contracts.
- State Privacy Laws Compliance – CCPA/CPRA (California)
- GDPR – EU privacy regulation (important if expanding internationally).
- CJIS Security Policy – If handling law-enforcement-related data for municipal utilities.
3. Which Are Necessary for us as a Utility SaaS
- SOC 2 Type II – Most common for US SaaS, directly boosts sales via RFP compliance. Covers ~70–80% of ISO 27001 and aligns with many privacy/security laws.
- CCPA/CPRA Compliance – Mandatory for California consumer data. Complements SOC 2 work and can be implemented in parallel.
- ISO/IEC 27001 – Expands credibility internationally; much of the work overlaps with SOC 2 (~70–80%).
- ISO/IEC 27701 – Adds strong privacy governance; builds on ISO 27001 (~20–30% extra work).
- PCI DSS SAQ (likely SAQ A) – If processing payments, even with Stripe/DOKU, you’ll still need the light self-assessment -
- We won’t need full PCI DSS certification (because Stripe/DOKU are PCI DSS Level 1 compliant and handle cardholder data).
- We will still need to complete a PCI DSS SAQ - but the lightest version, usually SAQ A, since we never touch or store cardholder data on your systems.
6. Others only if required specifically by our customers:
- FedRAMP, CMMC → Only for US government clients. (not needed if you get this data from state or municipal -> super costly process than that of SOC2 and ISO)
- GDPR, CCPA → Privacy laws; implement alongside SOC 2 work for efficiency. (State Privacy Laws Compliance)
- CSA STAR → Optional cloud security badge.
- NIST CSF/SP 800-53 → Mostly if targeting US gov or regulated sectors.
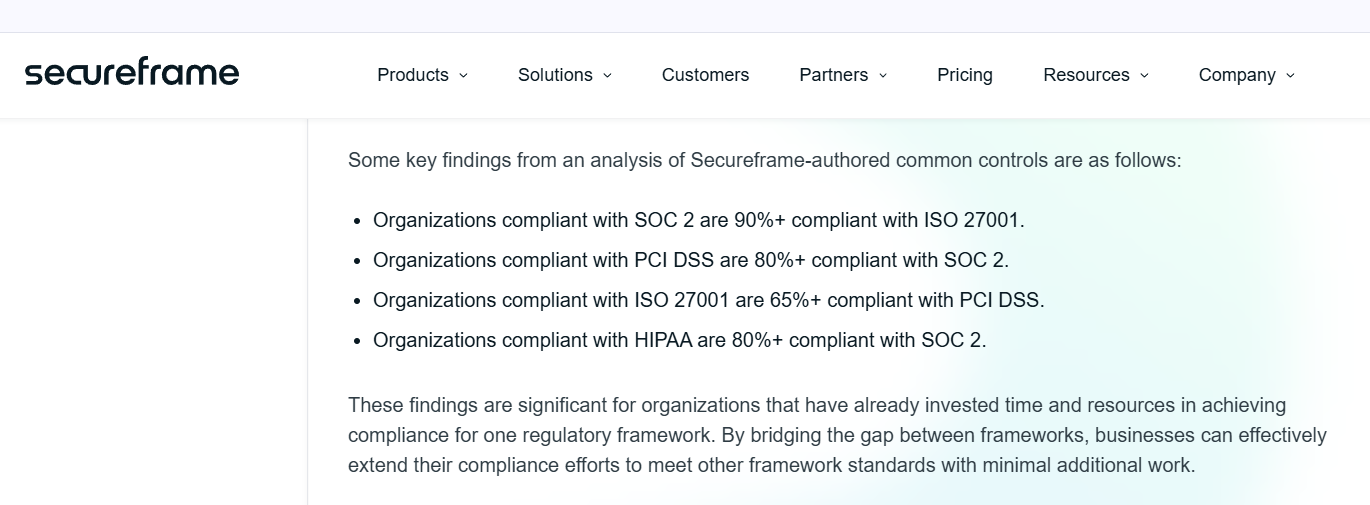
Overlap: Completing SOC 2 first covers ~90% of ISO 27001, 50% of NIST CSF, and key privacy/security requirements.
4. Why we’re choosing SOC 2 Type II as a top priority
1. Direct Impact on Sales & RFP Wins
- SOC 2 Type II is the most commonly requested security certification in U.S. SaaS procurement processes.
- Many RFPs, especially from utilities, municipalities, and enterprise clients, have a hard requirement for SOC 2 before you can even bid.
- Without it, we’re often blocked early in the sales funnel — losing deals before we can show the product.
2. Trust Signal for B2B and B2C Stakeholders
- Enterprise customers see SOC 2 Type II as proof that we’re not just claiming security — it’s been verified by an independent auditor.
- Consumers benefit indirectly, knowing their personal data is protected by rigorous controls.
- Builds confidence for potential partners, resellers, and integrations.
3. Fits Our Current Market Focus
- Our current customer base is mostly U.S.-based, where SOC 2 is the gold standard for SaaS security assurance.
- It’s faster to achieve than ISO 27001 (typically 6–9 months vs. 12+ months) and gets us to market-ready compliance quicker.
4. Long-Term Strategic Benefit
- Completing SOC 2 lays the foundation for other certifications with reduced cost and effort later (ISO 27001, ISO 27701, FedRAMP, etc.).
- Annual renewal keeps our processes sharp, preventing security drift.
5. Coverage Across Multiple Compliance Needs
- SOC 2 covers ~70–80% of the requirements in ISO 27001 (international standard) and ~50–60% of the NIST Cybersecurity Framework, meaning we get multi-framework progress from one effort.
- It also aligns with privacy laws like CCPA/CPRA by requiring strong controls for data protection, encryption, access management, and incident response.
5. SOC 2 Complete Overview
What's Exactly SOC 2 - https://bookstack.bynry.com/books/soc-ii/page/soc-2-overview
Certification Process - https://bookstack.bynry.com/books/soc-ii/page/certification-process-detailed-roadmap
Checklists - https://bookstack.bynry.com/books/soc-ii/chapter/checklists
6. Manual vs. Vendor Approach
| Factor | Manual Approach | Vendor Approach (Sprinto, Vanta, etc.) |
|---|---|---|
Implementation Speed | 9–12 months on average (especially first-time) | 4–6 months (with automation + templates) |
Team Effort Required | Heavy lift from internal team: security lead, engineering, HR, legal, ops | Vendor handles automation, reminders, control mapping; your team mainly provides evidence |
Documentation | Must write every policy, process, and evidence request manually | Pre-built, auditor-approved templates; fill in and customize |
Evidence Collection | Manual screenshots, log exports, and uploads — very time-consuming | Automated integrations pull logs from AWS, GCP, Okta, GitHub, Jira, etc. |
Audit Coordination | You manage timelines, communicate with auditor, ensure completeness | Vendor acts as project manager, keeps you on track, talks directly to auditors |
Knowledge Gaps | Risk of missing controls or misinterpreting requirements | Vendor already knows what auditors expect — reduces risk of rework or failure |
Cost | Lower out-of-pocket, but high hidden cost in employee hours | Higher subscription cost, but faster completion = faster revenue impact |
Renewal Prep | Repeat manual effort every year | Ongoing monitoring; renewal becomes a light lift |
Detailed : https://bookstack.bynry.com/books/soc-ii/page/soc-2-compliance-manual-vs-automation-vendor
7. Cost
[Actual costs will vary depending on the specific SOC 2 requirements we choose to implement, optimization actions taken]
Detailed Breakdown : https://bookstack.bynry.com/books/soc-ii/page/costs-monthly
- Baseline Today: ~$640/month.
- Minimal SOC 2 setup: +$416–$521 → $1,056–$1,161/month (+65–81%).
- With Cross-Region DR: +$566–$701 → $1,206–$1,341/month (+88–110%).
- Biggest cost drivers:
- AWS Inspector (~$216) – Continuous vulnerability scanning.
- Private networking (NAT gateways) (~$36–$80) – Required for RDS/ECS in private subnets.
- RDS Multi-AZ / DR replicas (~$129–$180) – High availability & disaster recovery. (considering the db instance size to remain the same, if the primary db size increases, these will also be increased)
- Optional heavy add-ons:
- Shield Advanced: +$3,000/month (only if mandated by a client).
- We can skip Inspector, avoid Multi-AZ & DR unless contractually required